Control multiple AWS organizations' access from a single AWS account

You have your own AWS account (in your organization), and several accounts in client organizations. This post shows you how to manage all accesses in a single account. So that you do not have to log out and log in every time.
Some values used in this post:
- Your organization ID:
123456789011, aliasmy-org. - Your client's organization ID:
110987654321, aliasmy-client.
Step 1: Allow users in my-org to access my-client.
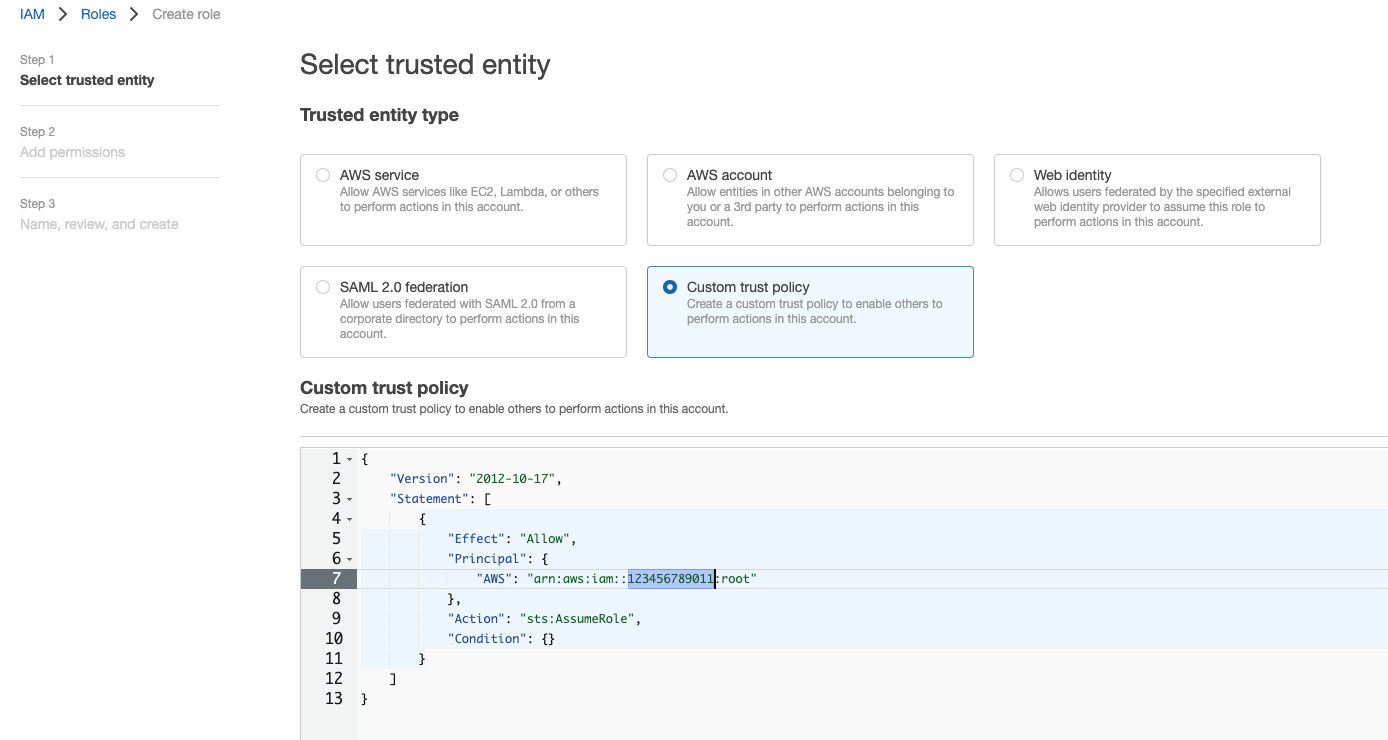
Login in to your account in my-client. In IAM console, create a role with the following trust policy. You have to remember the role name, to be used in the next step. Lets name the role to be role-for-my-org.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789011:root"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
Step 2: Access my-client from my-org account
Now, log out of your account in my-client, and log in to my-org's account.
Choose Switch Role.
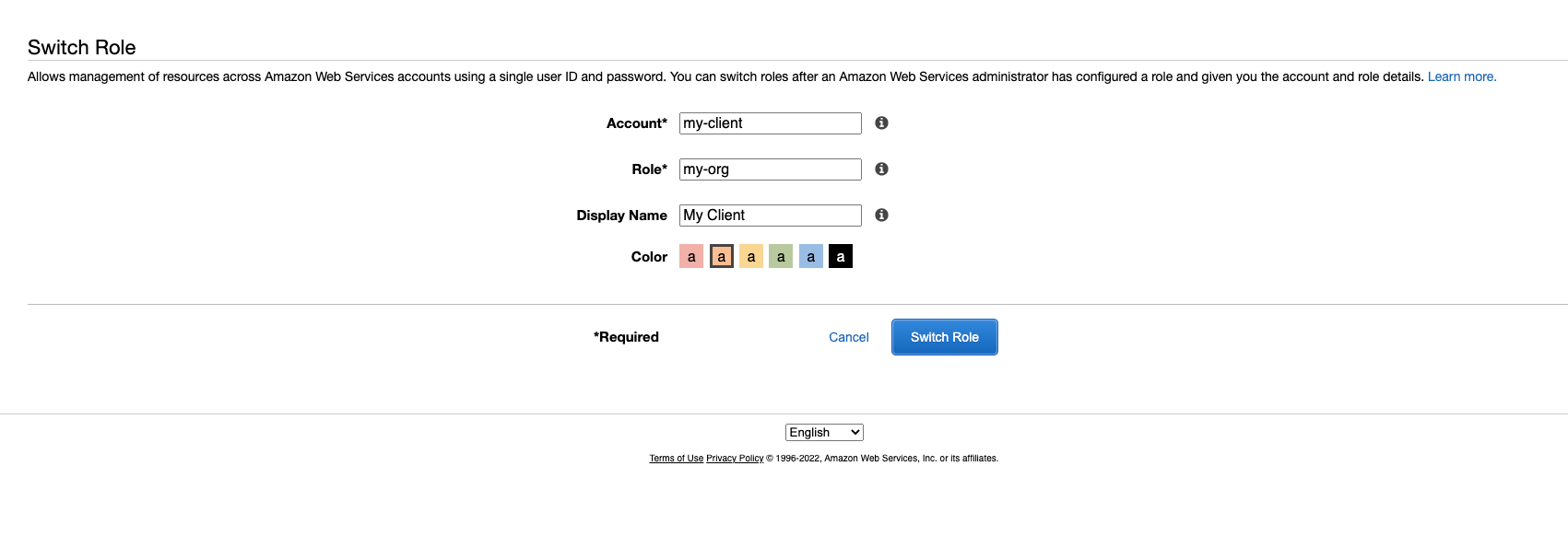
Enter appropriate information:
- Account: can be
my-clientor110987654321 - Role: the role name was created in step 1,
role-for-my-org. - Display name: any name for easier to organize.
Select "Switch Role".
Now you are done!.
Step 3 (optional) Access client resources from the command line via my organization account
Suppose that you have already added your my-org account credential in ~/.aws/credentials in a profile name my-org-account (or can be default profile, which does not matter)
[my-org-account]
aws_access_key_id = 123
aws_secret_access_key = abc
In ~/.aws/config add delegation profile as follows:
[profile my-client]
role_arn = arn:aws:iam::110987654321:role/role-for-my-org
source_profile = my-org-account
region = ap-northeast-1 in this sectionNow, whenever you run aws command line, add --profile pt to the command to switch the access to my-client organization.