Deadly simple sock proxy via ssh tunnel

You are in front of PC A, e.g. your company firewall
PC A is under a network with a firewall that blocks outbound traffic to some websites.
You also have a public server (PC B) that is not under any firewall (or the firewall rule is set up by yourself.
There is a way that allows you to view the blocked website. With the following ssh tunnel, you can use your browser under PC B's name from PC A
In PC A's command, execute
autossh -o "ServerAliveInterval 30" -o "ServerAliveCountMax 100" -D 1234 -CqNfT sammy@example.comCommand explanation
autossh: same command interface asssh, howeverautosshautomatically restarts the command if it is terminated.autosshneed to be installed manually. This command can be replaced withssh.o "ServerAliveInterval 30": for every 30 seconds, send a ping package to the server in order to prevent the ssh connection from being terminated due to inactivity.-o "ServerAliveCountMax 100": the number of server alive messages sent when the server does not respond, before terminating the connection.-Dsock channel port specifier-C: compress data-q: quiet mode, no warning-N: open SSH connection with no command to be executed-f: run background-T: do not allocate a TTY-terminal, save a tiny amount of memory
Now your localhost serves as a SOCKS proxy server at port 1234
Open firefox -> preference -> network setting -> Proxy -> manually Sock host. And set
Host: localhost
port: 1234
For Chrome (mac), execute http_proxy=socks5://localhost:1234 open -a '/Applications/Google Chrome.app'
For Mac with any browser, go to System Preferences, and choose "Network". In your currently connected network, click "Advanced", select the Proxies tab, check "SOCKS Proxy" and fill the host and port with "localhost" and "12345" respectively. Click "OK", then "Apply".
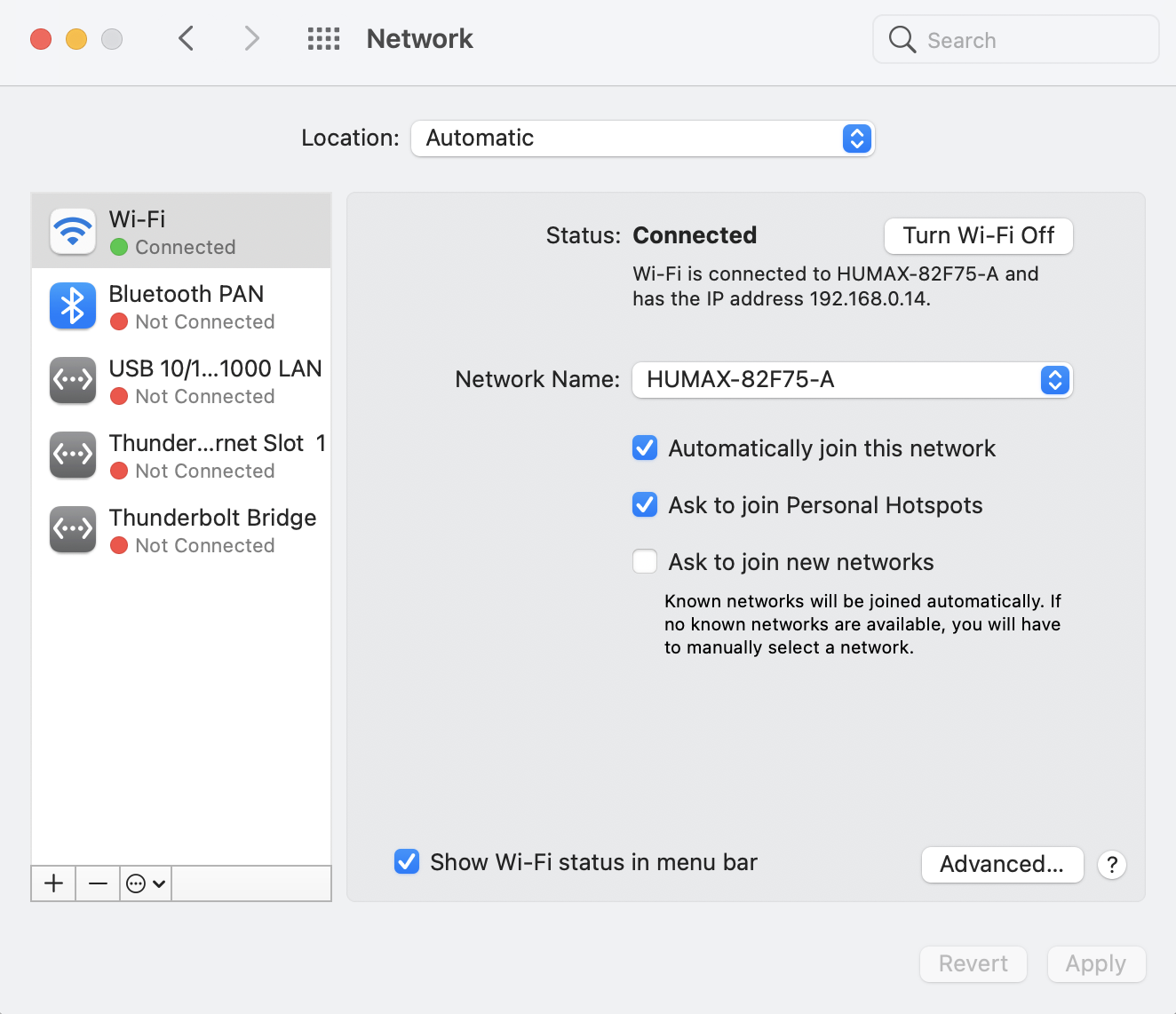
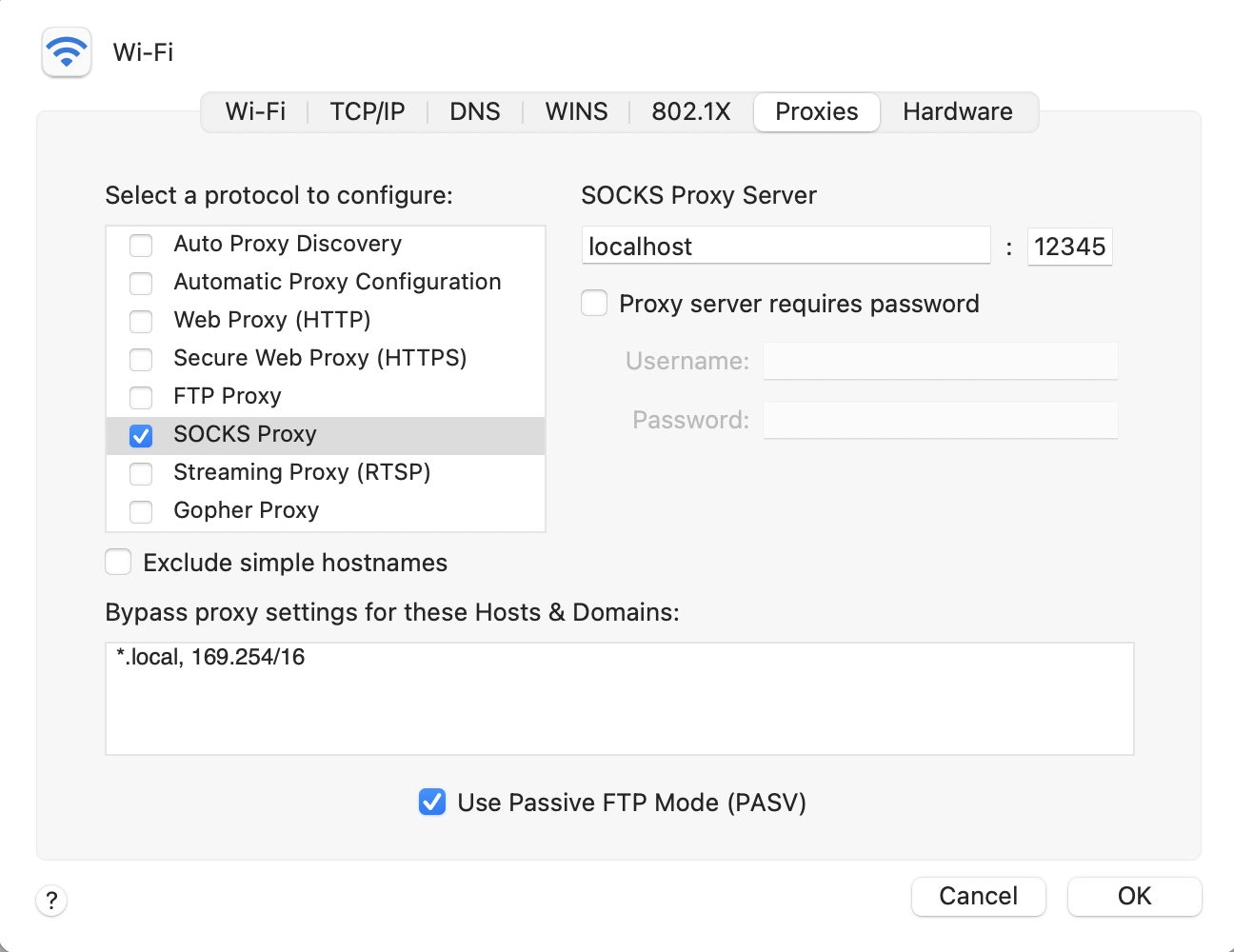
To open this sock connection whenever your PC startups. Refer to this blog post to set up a startup script.
Happy coding! <3