iptables note
This is more a note than a full tutorial. The full tutorial can be found from the link at the end of this post.
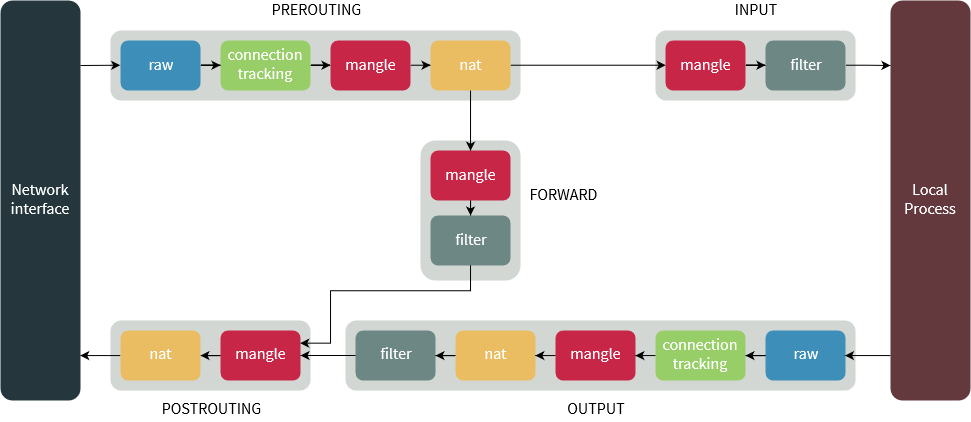
Type of table:
- filter
- nat
- mangle
- raw
- security
Type of chains (customizable):
- PREROUTING
- INPUT
- OUTPUT
- FORWARD
- POSTROUTING
Type of targets:
- ACCEPT
- DROP
- REJECT
- LOG (non-terminated)
- NAT
- DNAT
- CLASSIFY
- MASQUERADE
- (... check via
man iptables-extensions)
Common flags
Some rules have [!], which mean that ! is optional, added to negate the condition.
- -A: append rule (default)
- -D <chain> <rule num |or| rule spec>: delete rule
- [!] -i <interface> [+]: specify input interface. if + presents, match all interfaces having specified prefix.
- [!] -o <interface> [+]: output interface. similar to -i flag
- -t <table>: default is -t filter
- [!] --dport <port or port_start:port_end>: --dport 1000:2000 to specify all port between 1000 and 2000, inclusive
- -I <chain> [position]: if position is omitted. -I can be omitted and <chain> becomes first positional argument.
- [!] -p <protocol>: protocol is tcp or dcp
- -j <target>: jump to target. target can be chain or target. Some rules only allow specific targets. For e.g: nat table rules do not allow DROP target.
- [!] -s <ip>: source. can be xx.xx.xx.xx or xx.xx.xx.xx/len, so called CIDR notation.
- [!] -d <ip>: destination. ip format is same as -s.
- -m <module> [module params]: match extension module
To list existing rules, use
- -L: list rules
- -n: display port number rather ran application name
- -v: verbose additional information, such as in/out interface
- -S: simple mode. This flag should not be combined with any other flag. Useful to specify rule removal command.
Other flags
- -P: set default policy
- -F: flush all rules. to ask the user to keep or remove rule by one
- -E: rename chain
- -h: help
- -N: new chain
- -R: replace a rule
Note
iptables rules are in memory, all the rules stay in kernel memory and are wiped out after reboot. To persist in your setting, you must set up your own service to run the append command on each reboot or use an external tool. For example: follow this post to create your own startup script (service).
Source:
An In-Depth Guide to iptables, the Linux Firewall

